One benefit to Microsoft 365 is the ability to share data and collaborate with partners, customers, vendors and users who are external to your tenant. This benefit, however, can be a scary endeavor as information can be inadvertently exposed to outside entities. Couple this with the fact that tenants by default allow users to share data with outside individuals. Equally concerning is that configuring external collaboration can be complicated because there are multiple options available and there are many administrative consoles that need to be navigated.
The first step that must be performed when establishing external collaboration is defining what the objectives of the organization are and what will be shared. Here are a few options:
- Limit external collaboration to Teams chats
- Allow users to share files with external users
- Permit adding external users as members of Teams or Teams shared channels
Equally important is to define what external entities your users can shared with. Is it all users, is it a subset of users within a specific organization or is there a need to setup a trusted relationship at the organization (tenant level)?
This blog will focus on setting up a trusted relationship between two Microsoft 365 tenants. It will also demonstrate how users can setup Teams shared channels with users from the trusted organization.
Before jumping into the pool here is a quick overview of the options for establishing external collaboration. There are three flavors:
- B2B Collaboration: This is the more traditional method where external users are given guest accounts in your organization. Guest accounts need to be provisioned.
- B2B Direct Connect: Allows organizations to establish a trusted relationship with external Microsoft 365 tenants to allow for sharing data. Guest accounts do not need to be provisioned.
- Cross-tenant sync: Intended for organizations that have multiple tenants to provide seamless collaboration. This option blends B2B collaboration and B2B direct connect. A synchronization process creates guest accounts in the opposite tenant. This option should is not intended to be used across organizational boundaries.
Configure B2B Direct Connect
External collaboration is configured though cross-tenant access settings in the Microsoft Entra admin console. B2B direct requires the administrators in both tenants to enable cross-tenant access settings. In the tenant where the user’s accounts reside, known as the home tenant, an outbound connection needs to be created that lists the tenant where the resources reside – known as the resource tenant. The administrator in the resource tenant needs to create an inbound connection. Once this has been done in both tenants a trusted connection exists between them that establishes the groundwork for collaboration.
Note: these directions assume that the tenant defaults have not been changed.
Add the Other Organization's Tenant - Do This in Both Tenants
The administrators in both tenants need to perform the following steps to add the other organization’s tenant. From the Entra console (https://entra.microsoft.com) – navigate to:
- External Identities > Cross-tenant access settings > Cross-tenant access settings > Organizational settings
- Click +Add organization
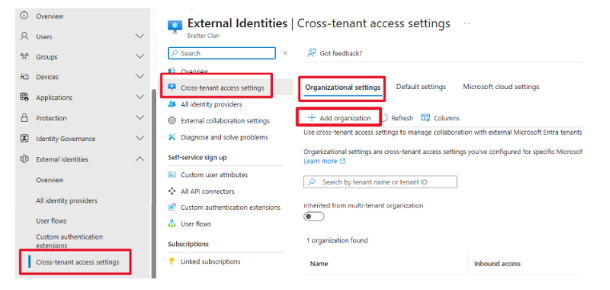
- In the Add organization flyout enter the Tenant ID or Domain Name. I recommend using the tenant ID, which you would need to get from the administrator of the source tenant.
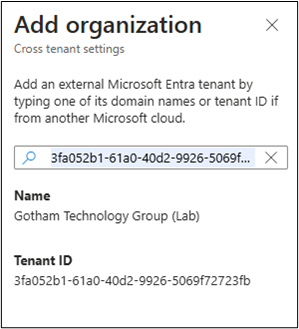
The newly added domain will be displayed on the Cross-tenant access settings page.
Configure the Inbound Access
The Inbound access is configured in the resource tenant. Under the Inbound access column in the Cross-tenant access settings page click on the Inherited from default link.
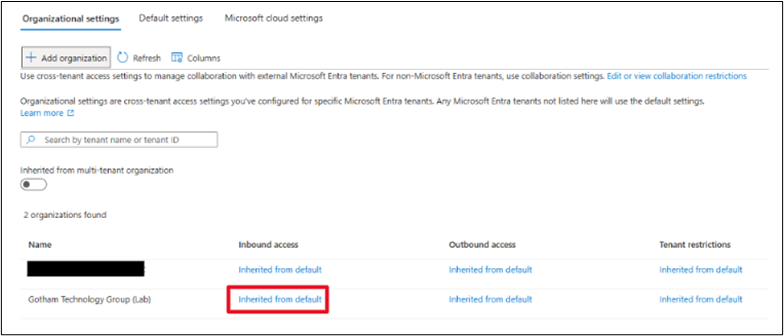
On the Inbound access settings page click on the B2B direct connect tab at the top of the page and then the Customize settings radio button and the Allow access radio button.
Under Applies to select either all users in the tenant or Select users and groups. If you choose Select users you will be presented with an additional field to enter the users/ groups you want to apply this policy to.
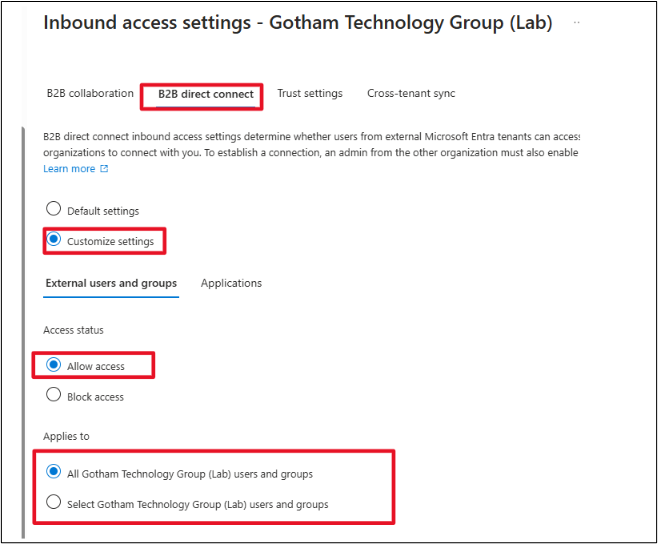
Next, click on the Applications tab, Allow access.
For Applies to click on Select external applications and then the Add Microsoft application link. Add Office 365. Of course, you could choose to add additional applications or all applications instead.
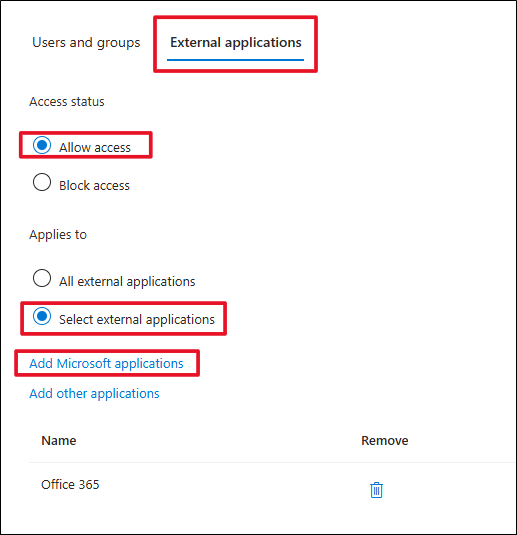
The inbound connection is established. Now, the outbound access needs to be configured in the resource tenant.
Configure the Outbound Access
The steps for configuring outbound access is identical to configuring inbound access except for some subtle differences. On the Cross-tenant access settings page confirm that the Organization settings tab is selected (which is the default), then select the Inherited from default link under the Outbound access column.
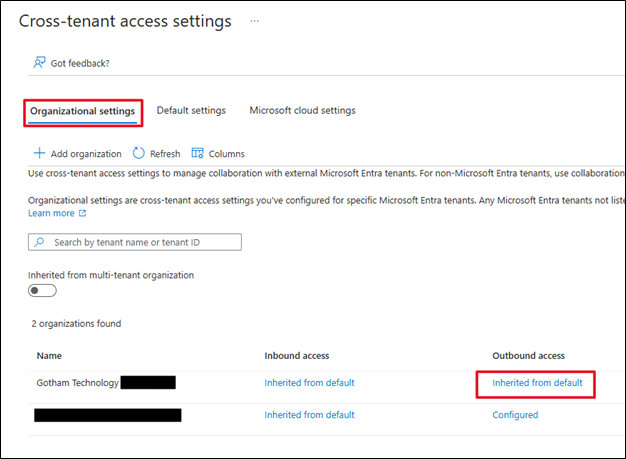
On the Outbound access settings page click on the B2B direct connect tab at the top of the page and then the Customize settings radio button and the Allow access button.
Under Applies to select either all users in the tenant or Select users and groups. If you choose Select users you will be presented with an additional box to enter the users/ groups you want to allow to collaborate.
After selecting the user an additional confirmation box will be displayed. The message is asking the administrator to acknowledge that the external tenant that has the outbound connection enabled will have limited access to contact info for users in this tenant.
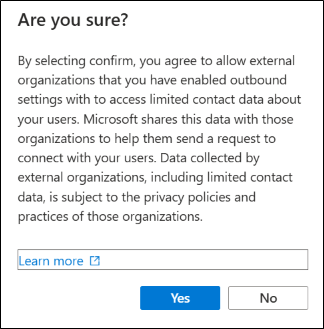
Next, click on the Applications tab, Allow access.
For Applies to click on Select external applications and then the Add Microsoft application link. Add Office 365. Of course, you could choose to add additional applications or all applications.
Reference the screenshots in the section above, which are identical.
At this point the trusted relationship is established between the two tenants.
Configure Teams Sharing
The next task to perform is to configure sharing within the Teams and the applications that Teams is integrated with. First, Teams policies need to be configured to allow users to create and work with Teams shared channels:
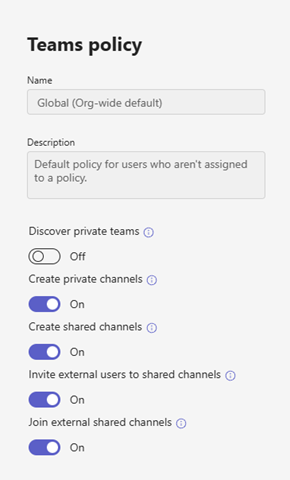
- From the Teams Admin Center expand Teams > Teams Policies > click on the Teams policy to update – by default there is a policy named Global (Org-wide default)
- In the Teams policy window make sure the following settings are enabled for the resource tenant:
- Create shared channels
- Invite external users to shared channels
- In the user’s home tenant confirm Join external shared channels is enabled
Secondly, external access also needs to be set. From the Teams Admin Center > Expand Users > External access. Confirm that the Teams and Skype for Business users in external organizations is set to either Allow all external domains or allow only specific external domains if the tenant is configured to use an allow list of external domains users can collaborate with. If so, make sure the external domain that was configured for B2B direct access is included in the list.
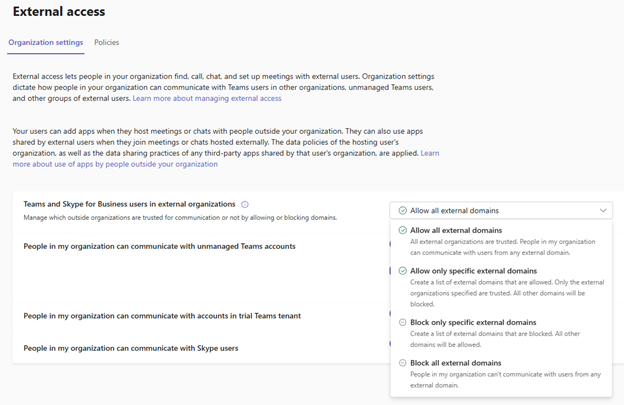
With Teams configured to support shared channels there are two more ingredients to configure:
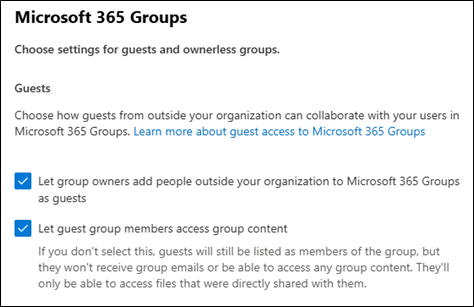
- Enable Microsoft 365 group sharing:
- This is done from the Microsoft 365 Admin Center: https://admin.microsoft.com
- Click on Settings > Org Settings > Microsoft 365 Groups
- Enable both Let group owners add people outside your organization to Microsoft 365 Groups as Guests and
- Let guest group members access group content
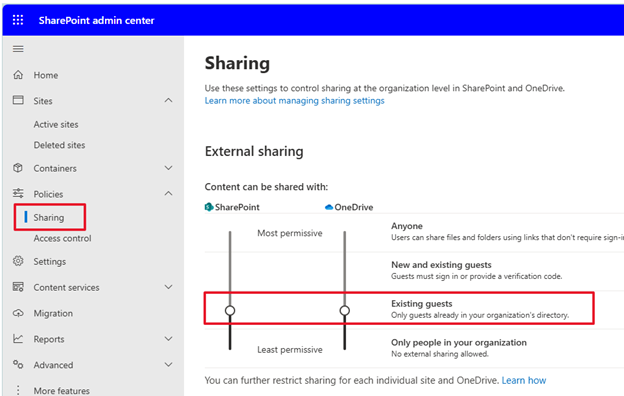
The last settings to configure are in the SharePoint Admin center where organization and site level sharing must allow guest access:
- From the SharePoint admin center click on policies > sharing
- Make sure the SharePoint external sharing slider is set to at least Existing guests.
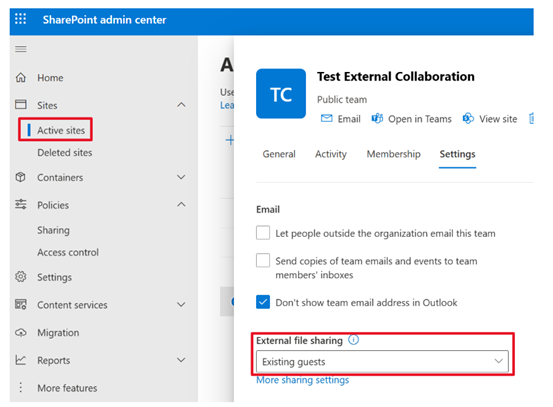
- For Site level sharing do the following:
- Expand Sites > Active sites > Click on the site name that will leverage shared channels
- Click on the Setting tabs and set External file sharing to Existing guests as a minimum
Note that all the settings in this section are enabled by default except for the SharePoint organization level sharing, which defaults to Anyone.
Additional Security Options
This section presents additional items that should be considered when setting up external collaboration. I won’t get into as much detail on these, but consider them ticklers that should likely be included as part of a collaboration strategy.
Inbound Trust Settings
For the tenant that is allowing inbound collaboration there are some additional security settings that should be considered. These settings determine whether your conditional access policies will trust MFA, compliant devices and Entra hybrid joined devices from an external organization to access resources in your tenant:
- Trust multifactor authentication from Microsoft Entra tenants: This enforces multifactor authentication from the user’s home tenant. This means that users do not have to enroll in MFA from the resource tenant, which simplifies the user experience. So, if a user’s account has MFA enabled in their home tenant that user will not have to enroll in MFA in the tenant where the resource is.
- Trust compliant devices
- Trust Microsoft Entra hybrid joined devices
The two devices-based options similarly allow the resource tenant to trust devices that are compliant or hybrid joined from the home tenant.
These settings can be accessed from the Cross-tenant access settings page under the Inbound access column for the domain of the user’s home tenant. Click on the Configured link and then the Trust Settings tab.
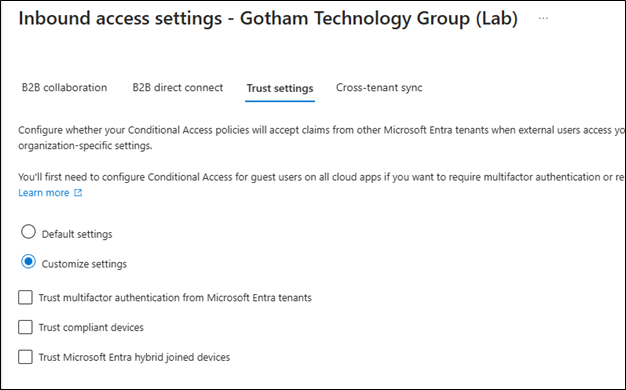
Note: If the conditional access policies in the resource tenant require MFA, the inbound trust settings must be configured to accept MFA claims from the user’s home tenant.
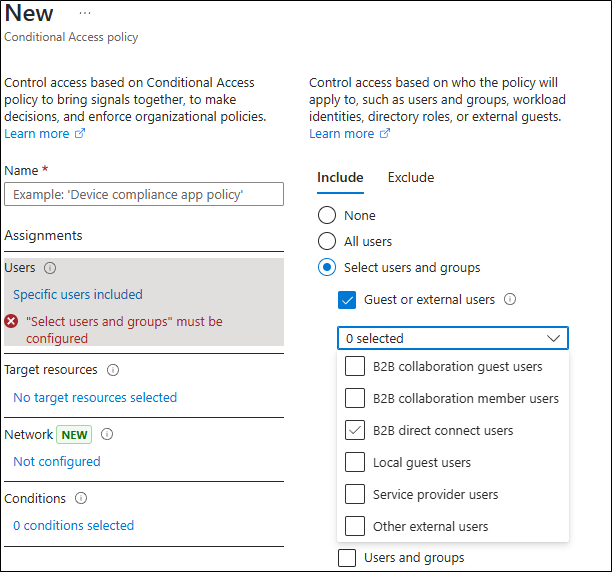
Conditional Access Policies
Conditional access policies can also be leveraged that target external users. For example, if you want to force external users to leverage MFA from your tenant. The Users control allows you to assign policies specifically to guest users.
Lifecycle Management for External Collaboration
There are two options that should be considered regarding lifecycle management for external collaboration. The first one is access reviews. In short access reviews provide a toolset to review who has access to what resources in a tenant. They can also be leveraged to remove access to resources.
Here is a good KB article to review: Plan a Microsoft Entra access reviews deployment - Microsoft Entra ID Governance | Microsoft Learn
Access reviews can be found under the Cross-tenant access settings page > Lifecycle management > Access reviews.
Another item that should be considered as part of an external collaboration strategy is Terms of use. This allows you to present terms and conditions that external users must acknowledge prior to accessing resources. This can be found under the Cross-tenant access settings page > Lifecycle management > Terms of use.
Using B2B Direct Connect with Teams
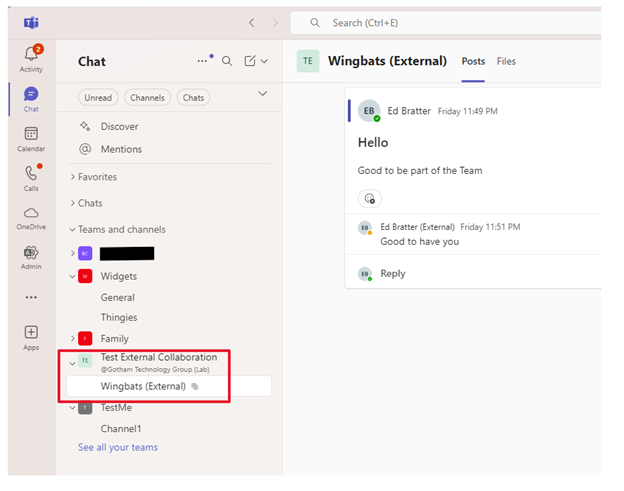
With B2B direct connect external users gain single sign-on access to B2B direct connect apps. At present, B2B connect supports Teams shared channels. With this, trusted external users can seamlessly access Teams shared channels without having to switch tenants or sign-in with a different account when working in the Teams application. This simplifies the user experience for the B2B direct users since they can access shared channels in their home instance of Teams. The shared channel shows up under the Teams and channels node along with the Teams and channels from the user’s home tenant. The shared channels are designated with (External) after the channel name.
The screenshot below shows the user logged into his home tenant. Under Teams and channels are the Teams this user is a member of in his home tenant and the shared channel in external tenant. The shared channel is designated with (External). The external user only has access to the shared channel and not any other resources within the Team or other apps in the tenant.
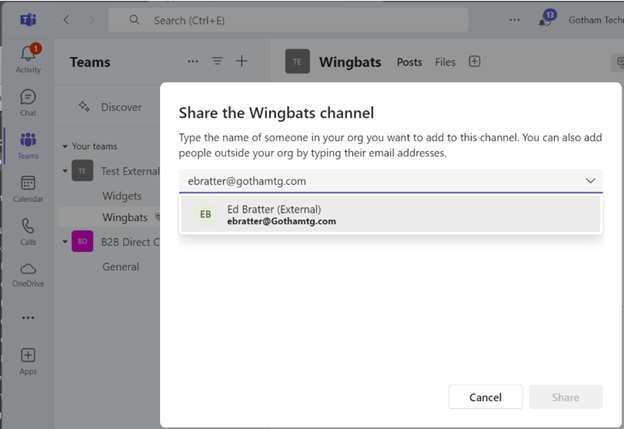
Additionally, in the resource organization Teams owners can search within Teams for users from the trusted external tenant and add them to the shared channels. Notice in the example below that an external user is being added to a shared Teams channel. When the Teams owner does a search for the external user, the search finds the user and designates it with an (External) after the name.
The B2B direct connect users do not have a presence within the resource tenant organization and thus won’t be seen in other apps that do not support B2B direct connect.
The B2B direct connect experience differs from B2B collaboration in that B2B collaboration users need to have guest accounts and must be invited to a Team. The invited user receives an email of the invitation to participate in the Team and has to acknowledge the invite. Guest users cannot participate in shared channels but can be a member of a Team and have access to standard channels.
When invited to Teams shared channels, users will not receive an email invite like they when they are setup as guest in the tenant.
Finally, be aware that the non-B2B direct connect settings shown above can impact external collaboration for not only B2B direct connect users, but also B2B collaboration users. If this is not desired, then it is important to review the B2B collaboration settings and make sure they are set to meet the needs of the organization.