If you are confused about Azure Active Directory (AD) hybrid join, what it is, when to use it, and how to set it up, keep reading. Azure AD hybrid join is for Windows devices and is one of three methods to associate devices to Azure AD: Azure AD registered, Azure AD joined, and Hybrid Azure AD joined. This article focuses exclusively on Azure AD hybrid joins.. If you are using federated management via AD FS or a third-party tool, the hybrid join process is slightly different.
What is Azure AD Hybrid Join?
A hybrid Azure AD join is an identity management model where Windows machines are joined to an on-premises AD domain and also joined to Azure AD. To hybrid join a machine the account used to login into the machine must be in the on-premises AD that is also synced to Azure AD.
Hybrid join provides the following benefits:
- The device behaves like any other domain joined machine meaning:
- Group policies are applied
- The user is assigned a Kerberos ticket which provides access to on-premises resources and AD integrated applications
- The Azure AD join adds the following:
- On login the user receives an Azure AD user token (This is in addition to the on-premises Kerberos ticket) which is used to access Azure AD integrated resources such as Exchange, Teams, and third-party SAAS solutions or apps that integrate with Azure AD, etc.
- Device-based conditional access policies. Hybrid join is particularly important because that is how to define organization owned devices when establishing policies that require organization ownership of Windows devices to access Microsoft 365 resources. Neither Azure AD register nor Azure AD join satisfies the requirement for organization ownership.
- Synchronization of Windows settings via enterprise state roaming
- Windows Hello for Business
- Backup of BitLocker recovery key in Azure AD
Hybrid join does not provide:
- The ability to change your AD password (and sync it to the local cache) when the machine does not have line of site to domain controllers
- Allow users to login to the machine with cloud managed Azure AD accounts
In essence, hybrid join requires line-of-site to on-premises domain controllers on a periodic basis. For machines that are typically off network, VPNs satisfy this requirement. For organizations that are looking to lead with a cloud presence or transition away from on-premises dependence hybrid join is probably not the right fit. Instead, consider doing an Azure AD join with Intune for device management.
Preparing / Performing Hybrid Join
A hybrid join is a multi-step process where several tasks need to be carried out for the hybrid join to complete successfully:
- Join the machine to the on-premises AD
- Azure AD Connect syncs the computer object to Azure AD (In a similar fashion to how it syncs user and group objects)
- A user signs into the machine to complete the hybrid join process. For this last step to complete the machine must have line of site to domain controllers at login.
Azure AD Connect needs to be configured to facilitate the hybrid Azure AD join, which is described in this KB article: Configure hybrid Azure Active Directory join | Microsoft Docs. Make sure that you add the Organizational Units that host the computer objects that you intend to hybrid join to the AD Connect synchronization scope. Also, confirm that existing PCs are in those OUs and that newly domain joined PCs are placed into the correct OU.
When configuring AD Connect for hybrid join, an AD service connection point (SCP) will be created. The SCP is leveraged by the computer to retrieve the details of the Azure AD tenant it is going to hybrid join to. It does this by doing an LDAP query against AD. Once the SCP is created Windows machines attempt to register themselves in Azure AD. This will initially fail until the following steps are completed, which will happen automatically:
- The UserCertificate property of the computer object in AD is populated with a self-signed certificate that is created by the computer. The computer will create this certificate after detecting the SCP.
- AD Connect syncs the computer object to Azure AD. Note, if the step above does not complete, then AD Connect won’t sync the object.
After the steps above have completed and AD Connect performs a sync a computer object will be created in Azure AD. At this point, you might want to confirm that the computer object is listed in Azure AD. To do so open the Azure AD Admin Center: Go to Azure Active Directory > Devices > All Devices. This will display all devices associated to Azure AD (Including those that are registered and Azure AD joined). The columns of relevance are:
- OS: displays the OS type such as Windows, iPhone, iPad, Android, etc.
- Join type: this will be one of the following:
- Azure AD Registered
- Azure AD joined
- Hybrid Azure AD joined
- Registered: This column will display one of the following values:
- This state confirms that AD Connect has synced the computer object to AAD, but that the hybrid join is not complete yet. As such, the machine is not considered hybrid joined meaning the benefits shown above are not available yet.
- The date/time the device completed the hybrid join.
If there are a lot of devices listed a filter can be set to show inly hybrid joined machines: Join type > hybrid Azure AD joined. At this point the computer object should be displayed with the Registered value set to pending (See screen shot below). Notice the machine above it has completed a successful hybrid join with the time/date that occurred.

If the Windows machine was previously Azure AD registered there may be duplicate entries for the computer object. Duplicate entries will also exist if multiple users share the same machine. In this scenario the machine showing the Azure AD Registered state will be removed after the same user logs into the machine once the hybrid join has completed. The removal for additional users will occur after they log in. Automatic device cleanup requires Windows 10 version 1803 and higher. For previous versions, cleanup the Azure AD registered state before initiating the hybrid join process.
You can prevent your domain joined device from being Azure AD registered by adding the following registry value to HKLM\SOFTWARE\Policies\Microsoft\Windows\WorkplaceJoin: "BlockAADWorkplaceJoin" = dword:00000001.
Once ADConnect has done its job and the computer object is showing a pending state in Azure AD, the next step is for a user to log into the machine. For the hybrid join to complete, the machine must have line-of-site to a domain controller. If it does not, the registered state will continue to show pending.
After login the following steps must execute to complete the hybrid join:
- A Task Scheduler event will kick off that triggers on logon that will complete the hybrid join. Remember, for the hybrid registration to complete the machine must have line of site to a domain controller. A machine with an active VPN connection will satisfy the line of site requirement but one of the following must also be performed to complete the join:
- Lock the desktop and then log in again. This will trigger the task to run again.
- Manually run the Task Event (this requires admin access). From Task Scheduler navigate to Task Scheduler Library > Microsoft > Windows > Workplace Join > Right click the Automatic-Device-Join task and select Run
- Run DSRegCmd /join from an administrative command prompt.
- This can also be triggered remotely: PsExec -s <\\Windows Machine> cmd and then type dsregcmd /join
See the screenshot below which shows the Task Scheduler task that needs to execute to complete the hybrid join.
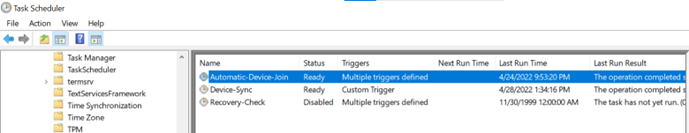
After a user successfully signs into a machine with line-of-site to a DC and the Automatic-Device-Join task executes, the device completes the hybrid join process. At that point Azure AD provides a certificate to the Windows machine and the registration column in the AAD Admin Center changes from pending to the date / time the machine completes its registration. The device is now hybrid joined.
The successful join to Azure AD will result in two certificates being added to the personal computer store:
- The self-signed computer-generated certificate, which kicked off the Azure AD hybrid join process
- The Azure AD certificate passed to the machines once the registration in Azure AD completes
These certificates are shown below.
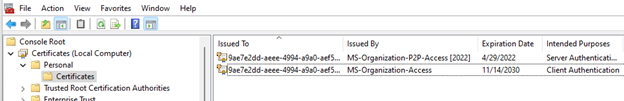
With a successful hybrid join, users who sign in will receive an Azure AD user token, known as a primary refresh token or PRT, which is used to authenticate to Azure AD applications and services.
DsRegCmd is a command line utility that is your friend when it comes to understanding the status of devices in Azure AD. Below is an example of it confirming a device is hybrid joined and confirms the user who is logged in has an Azure primary refresh token (PRT) which is used to authenticate to Azure resources and provide for single sign-on. The screen shot below shows the results of Dsregcmd /status:
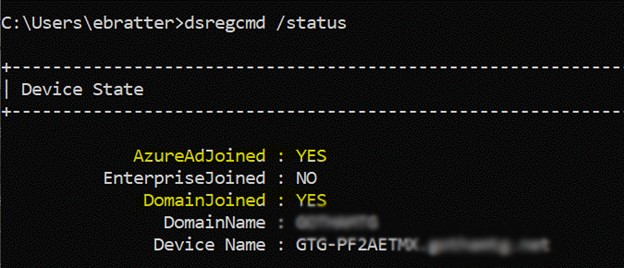
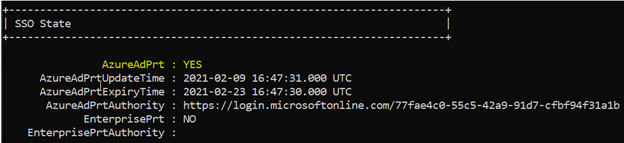
The important values are highlighted in yellow. AzureAdJoined confirms the machines are joined to Azure AD whereas DomainJoined confirms the machine is connected to the on-premises AD environment. AzurePrt should say yes, which provides for single sign-on to resources that leverage Azure AD for authentication. Together, these confirm a successful hybrid join to Azure AD. There are additional parameters that this command offers so take a moment to do some research on it.
Troubleshooting Azure AD Hybrid Join
If you encounter issues with hybrid join here are some options to help rectify the problem.
First, and most obvious is to confirm that the steps shown above have completed successfully. Also run dsregcmd /status and check the three values described above. Understanding where the registration breaks down is helpful in determining where the problem might be. For example:
- Is the computer object in AzureAD? If not, did AD Connect run a sync? If so, confirm that the UserCertificate attribute of the computer object has been populated. This is the machine-self signed certificate. If this does not exist, the machine object will not sync to Azure AD
- Does the computer object in AzureAD show a registration status of Pending? If so, the likely cause is that a user has not logged onto the machine when it had line of site to a domain controller. Remember that the user who logs in must log in with an AD account that syncs to Azure AD.
Next, check Event Viewer on the PC having an issue. There are two logs to check:
- Application and Services > Microsoft > Windows > Workplace Join > Admin
- Application and Services > Microsoft > Windows > User Device Registration > Admin
Researching errors in these logs should help resolve the problem.
Another option is to download the Device Registration Troubleshooter Tool (DSRegTool) from Device Registration Troubleshooter Tool - Code Samples | Microsoft Docs. This is a PowerShell script that is used to troubleshoot device registration issues. It needs to run from an administrative PowerShell session. It provides a menu of items to test and validate Azure AD registration.
Also, keep in mind that completing a hybrid join can also be an exercise in patience. If you know all the steps have completed – be patient. Give the system some time to catch up. So go grab a cp of coffee and check back in later.
Here are some additional helpful links for troubleshooting:
Troubleshooting hybrid Azure Active Directory joined devices | Microsoft Docs
Pending devices in Azure Active Directory - Active Directory | Microsoft Docs