Many look forward to the Fall when Apple releases its newest version of iOS with the new features and toys it presents. One of this year’s improvements offers a vastly simplified process for enrolling personal (BYOD) devices into a mobile device management (MDM) solution such as Intune. The current method requires installing both the Company Portal and the Microsoft Authenticator app, and requires a dance through a maze of screens and jumping between applications to successfully enroll a device. The new method simplifies this process by eliminating the requirement for the Company Portal and reduces the number of screens and prompts to complete the enrollment.
The downside to this is that Apple has pulled support for profile-based enrollment (in Intune speak, this is referred to as user enrollment with Company Portal) in iOS 18. If a user attempts to enroll a device with profile-based enrollment, the device will throw a message stating that profile driven user enrollment is not supported.
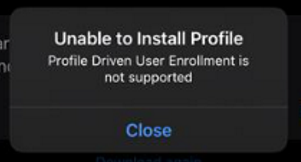
Older versions of iOS continue to support the older enrollment method and the device can be successfully upgraded to iOS 18. However, if the user unenrolls the device, re-enrollment will need to be done with the newer enrollment method. Devices that are already enrolled are still supported in Intune with the older method.
Apple calls the new enrollment method account-based enrollment or account driven user enrollment (Intune). A user initiates enrollment by navigating to iOS settings > General > VPN & Device Management and logging in with their Entra ID credentials, which should federate with Apple, serving as the user’s Apple Managed ID.
Now for the bad news: though device enrollment has been simplified for users, there are additional configuration steps that Intune admins must complete to support account driven user enrollment. The steps are documented below.
Configuring Account Driven User Enrollment
Account driven user enrollment is anchored by publishing a JSON file that contains information about the Intune tenant the device will be enrolled in. Upon entering Entra ID credentials to initiate Intune enrollment, the device looks at the domain name that is derived from the user’s credentials and then searches for the JSON file. Once the tenant has been identified, the enrollment process is launched.
Here are the steps to configure account driven user enrollment:
Create a JSON file
If you are not well versed in creating and managing web sites, publishing a JSON file may seem foreign to you. In this case, ask the developers of the company website to perform the steps below:
- Set up and publish an HTTP well-known resource file on the same domain that employees sign into
- Set the content type to application/JSON
- Publish the file on a domain that can handle HTTP GET requests
- Use the following format:
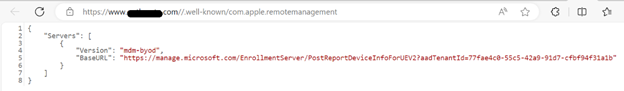
- {"Servers":[{"Version":"mdm-byod", "BaseURL":"https://manage.microsoft.com/EnrollmentServer/PostReportDeviceInfoForUEV2?aadTenantId=YourAADTenantID"}]}
To confirm the file has been published, browse to the following location: www.<Your domain>.com/.well-known/com.apple.remotemanagement and the results should look similar to the screenshot below.
Here is a link that might help if you are hosting your website on an IIS server: Apple remote management, How to set up .well-known directory on Windows IIS server
Intune Configuration
The remaining steps are performed in the Intune Console.
Create a New Apple Enrollment Profile
- Devices > iOS / iPadOS > Enrollment > Enrollment types > Create profile. Give the profile a name and set the Enrollment type to Account driven user enrollment. Then assign it to a group of users and set the priority if necessary. At a minimum, it probably needs to have a higher priority than the older user enrollment with Company Portal profile that exists, though the goal should be to remove this profile.
Setup Just in Time (JIT) Registration via a Configuration Profile
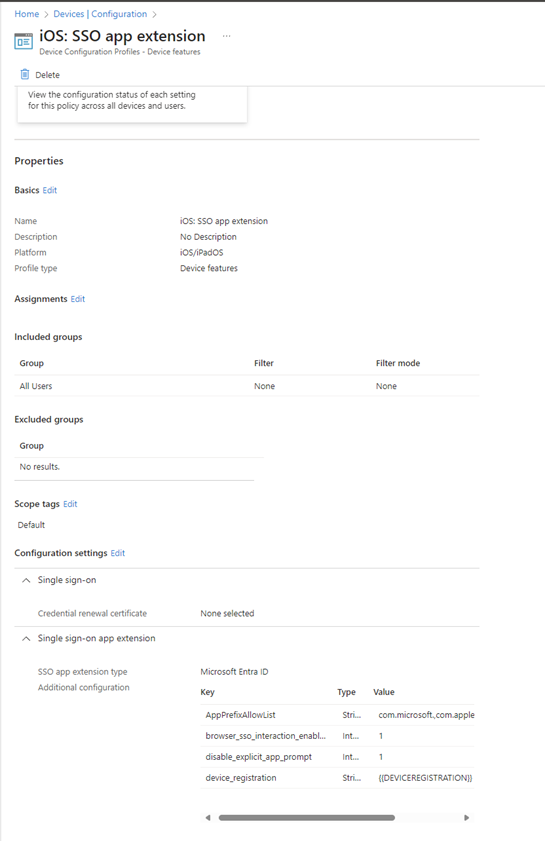
- Devices > iOS / iPadOS > Configuration > Create New Policy > Templates > Device features. Give the policy a name.
- Expand Single sign-on app extension
- Under SSO app extension type, select Microsoft Entra ID
- Enable shared device extension > Not configured
- Add the following keys under Additional configuration:
|
Key
|
Type
|
Value
|
|
AppPrefixAllowList
|
String
|
com.microsoft.,com.apple.
|
|
browser_sso_interaction_enabled
|
Integer
|
1
|
|
disable_explicit_app_prompt
|
Integer
|
1
|
|
device_registration
|
String
|
{{DEVICEREGISTRATION}}
|
- Click Next
- Complete the configuration profile
The screenshot below shows an example of the configuration profile.
Publish the Company Portal
There are two methods to make the Company Portal available to users:
Once these steps have been completed, the new enrollment method should be available.
Concluding Thoughts
This newer enrollment method does make it easier for users to enroll their personal devices into Intune, though it does require more configuration work for Intune administrators. Once enrolled, account-based enrollment is identical to profile-based enrollment in terms of the user experience on iOS devices. The administrative experience in Intune is also identical.
Additionally, account-based user enrollment also applies to the latest version of macOS.
This change does not impact automated device enrollment (ADE) or profile-based device enrollment (device enrollment via Company Portal). Interestingly enough, the steps above provide support for web-based enrollment. Web-based enrollment provides a simplified method to do device-based enrollments in the same manner that account-driven enrollment simplifies user enrollment with Company Portal. Of course, this might make one wonder when Apple will drop support for profile-based device enrollment.