In the ever-evolving landscape of cybersecurity threats, phishing and ransomware emails remain persistent challenges for organizations. While technology plays a crucial role in minimizing the impact of such threats, user-based training is equally essential. Many corporations have adopted mandatory training programs that aim to educate employees and test their ability to identify and respond to suspicious emails. In this blog post, we will explore the effectiveness of user training and how Microsoft Attack Simulation can be a valuable tool in this endeavor.
User Training: A Proven Strategy
Despite the implementation of advanced email filtering technologies, phishing and ransomware emails can still find their way into a user's mailbox. User training is a proactive approach to minimize the risk. Many organizations conduct quarterly or annual training sessions, often combined with simulated phishing and ransomware campaigns. These campaigns serve as practical tests to determine whether employees can recognize suspicious emails or if they inadvertently click on them, potentially compromising security. Employees who fail these campaigns are typically required to undergo training again, and this strategy has shown considerable success in enhancing cybersecurity awareness.
Microsoft Attack Simulation: An Overview
For organizations not conducting regular employee testing, Microsoft offers Attack Simulation Training, an included feature for those with Microsoft Defender for Office 365 Plan 2 or equivalent subscriptions. To access this feature, users can visit security.microsoft.com. Administrators will find the “Attack simulation training” option on the left pane. From here, you can create simulations, choosing from a range of techniques such as Credential Harvest, Malware Attachment, and OAuth Consent Grant. Each technique simulates different types of threats.
Administrators can then select the payload for the simulation, the content of the payload to understand what will be emailed to employees, which groups of employees will receive the test email, and a phish landing page template that employees will see if they click on the simulated phishing link.
Sending the Simulation
Once all settings are configured, the simulation is ready to be sent to the selected employees.
Once the simulation is sent, the employee(s) will receive an email like the following:
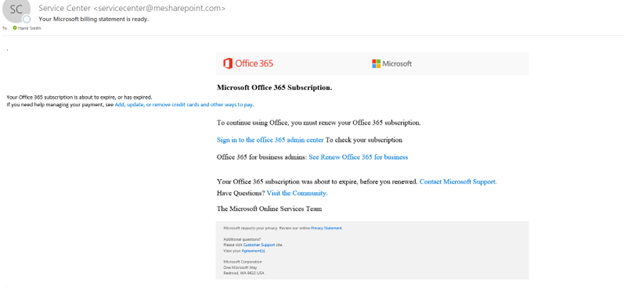
For the purposes of this blog, I will click on the link to “Sign in to office 365 admin center,” which presents a very familiar Microsoft logon prompt.
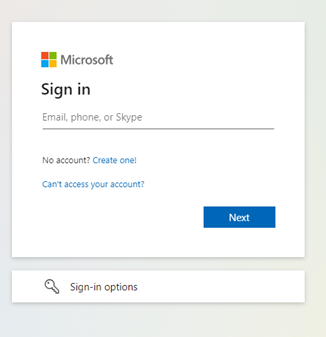
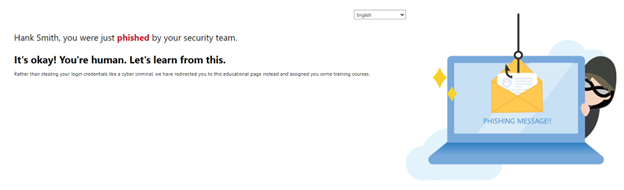
I logged in with bogus credentials, which provided the page to take training.
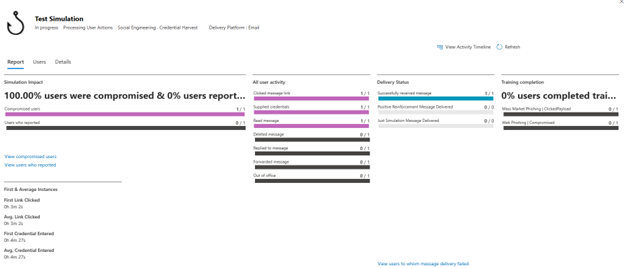
Reviewing the Results
Administrators can monitor the simulation’s progress and review the results, identifying which employees clicked on the link, supplied credentials, and other relevant information.
Wrapping Up
Microsoft Attack Simulation is a valuable tool for educating employees about various ransomware and phishing campaigns. It provides a proactive approach to cybersecurity by training employees to recognize and respond to threats effectively. This approach, combined with technology, can significantly reduce the risk of falling victim to phishing and ransomware attacks, making it an essential component of a comprehensive cybersecurity strategy.