One of the benefits of Microsoft 365 is the ability for users to collaborate and share with co-workers, clients, vendors, partners, and people external to the organization. This benefit, however, comes with a downside; users can either purposely or inadvertently expose information that the organization would not want shared externally.
To complicate matters, newly established tenants leave the door wide-open for publishing data to external entities. As a result, users can share data with outside individuals, which may go against the organization’s wishes. With this in mind, it is imperative for tenant administrators to properly lock and secure the tenant before allowing users to access it.
This article demonstrates the dangers that a new tenant presents with respect to sharing information and the steps to control and lock down access that meets the needs of the organization.
The Dangers of the Click of the Mouse - Existing Landscape
As tenant administrators know, when users are assigned licenses, they can immediately access the services, features, and applications that the license provides. From a sharing perspective, this means that users can share OneDrive hosted documents and folders, SharePoint sites, and Teams with individuals outside the organization. Additionally, Microsoft 365 Group owners can add people outside the organization as guests and guests can access group content. Perhaps even more worrisome is that users can share documents with anonymous users outside the organization.
Here’s an example that should scare any tenant administrator. Jane Doe is working in her OneDrive site and wants to share a document with Bill Smith who works for ABC Corp. Her intent is to share the document named My Shared Doc shown below with Bill.
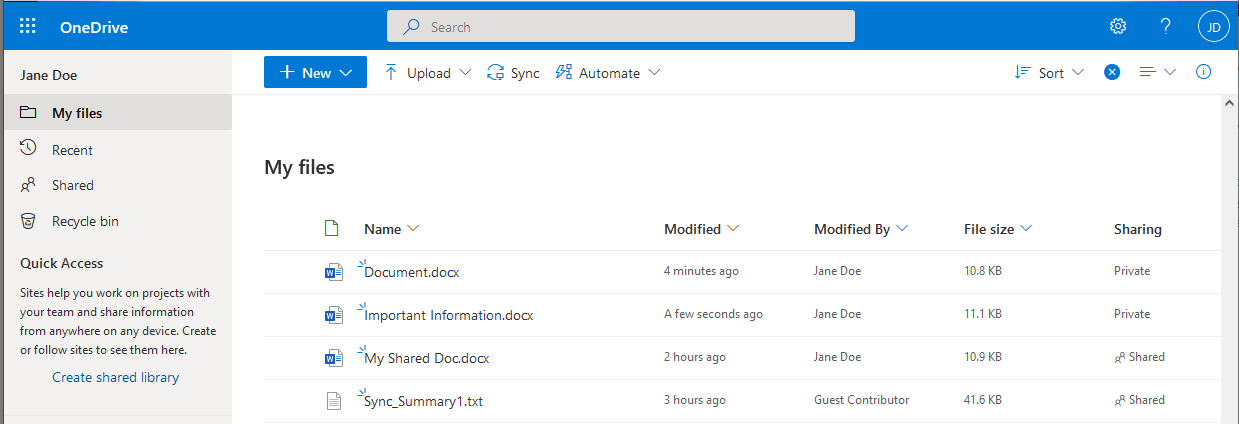
By mistake Jane clicks on the wrong document, Important Information, to begin the process of sharing.
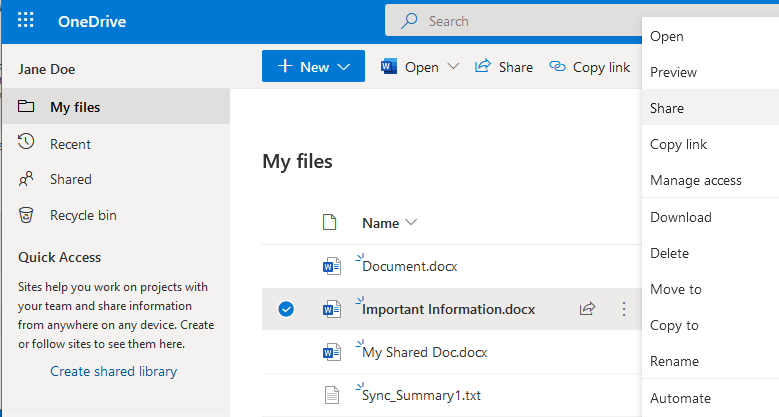
This brings her to the Send Link page. This is where the user defines who the document will be shared with. Since the tenant is running in a default state, no restrictions have been applied as to who the document can be shared with. Notice the default on this page is to allow anyone with the link to edit the document.
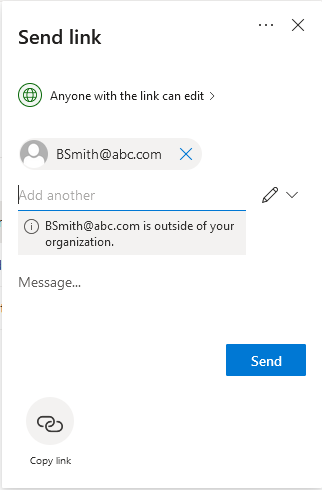
Clicking on the pencil allows the user to add restrictions to the shared document such as setting an expiration date for the shared access, password protection, or changing the type of access to view only. The defaults provide for minimum security settings and maximum access.
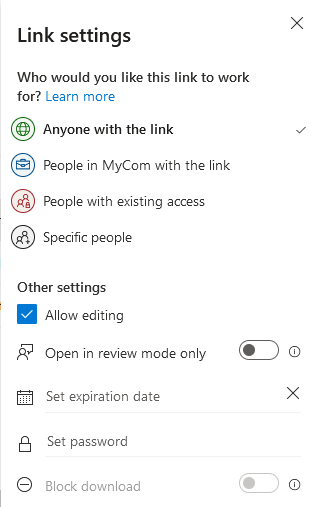
After Jane completes the process to share the document, Bill receives an email informing him that Jane has shared a file with him. The email includes the link to access the document.
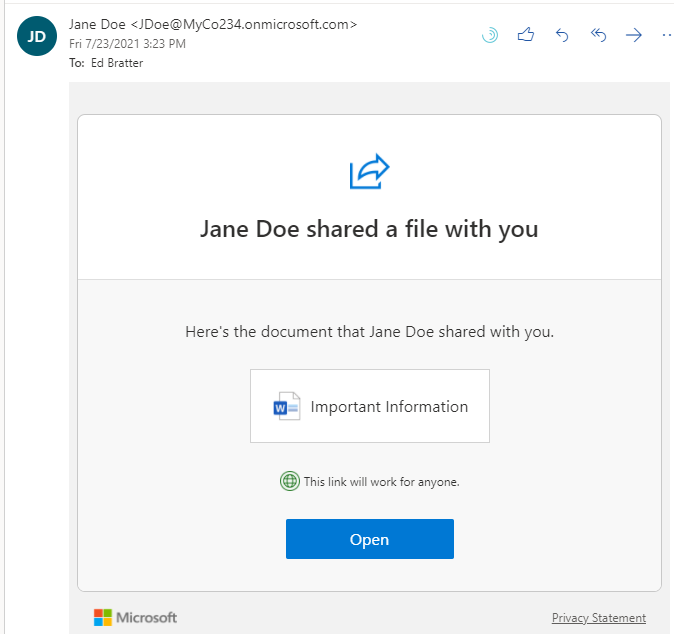
Clicking the link will open the document. If no restrictions have been implemented, the document will open in a browser or optionally any application that can edit the document type.
To this point Jane has been permitted to share a document with an external user with no controls put in place by the organization to control and limit access. That user can access the document via the provided link and makes changes to it. This access never expires.
Let’s continue with the example, where it takes a dark turn. Bill’s mailbox gets hacked and a bad guy gets the link to the document. The bad guy then opens the document and makes some changes to it. Next time Jane opens the document she sees the following:
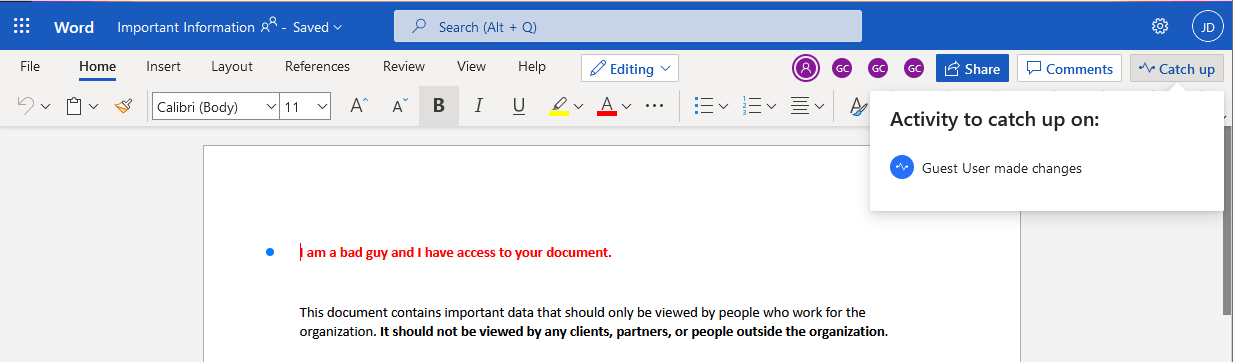
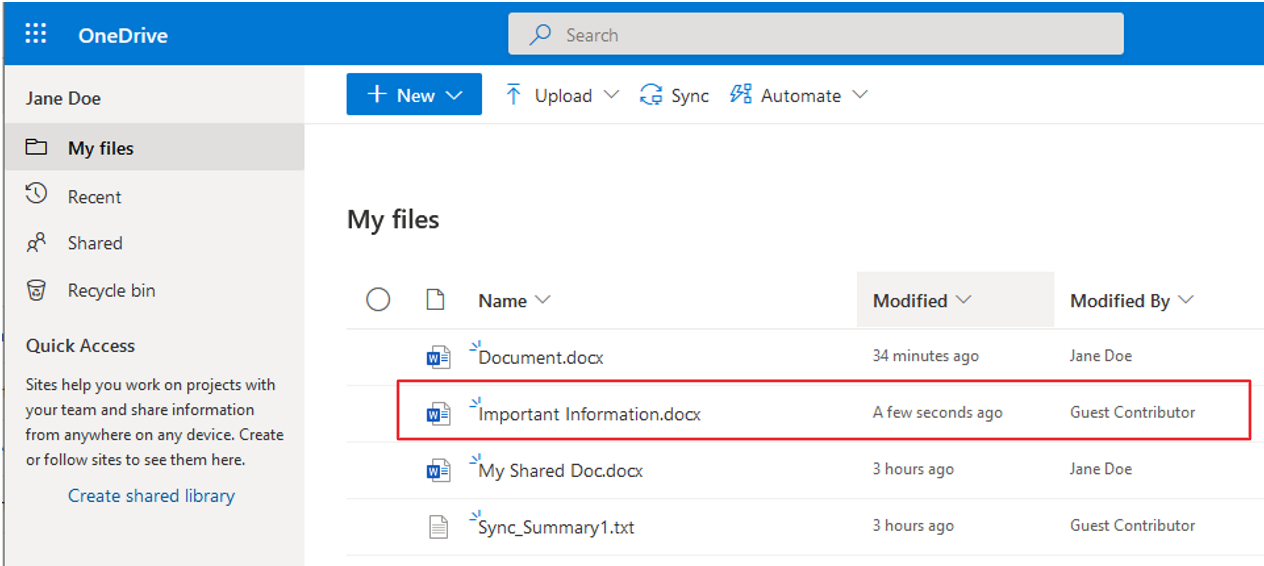
Notice that Jane’s OneDrive site shows that a Guest Contributor made modifications
 The Solution
The Solution
The good news is that this can be fixed. The tenant can be configured to allow for more controlled access based on the needs of the organization. This section reviews the settings and options that are available to provide for the level of access that meets the requirements of the organization.
Before making configuration changes, it is important to define what the external sharing requirements are. This should coincide with general governance and retention policies. Once the objectives have been defined, it is time to dig into configuration settings. A comprehensive sharing policy must be implemented in multiple locations that cover various Microsoft 365 services, including the following:
- The Azure Active Directory Admin Center
- The Microsoft 365 Admin Center
- The SharePoint Admin Center, which covers both SharePoint and OneDrive
- The Teams Admin Center
Azure Active Directory Admin Center
Configuring and controlling external file sharing begins in the Azure AD Admin Center. All sharing is governed at this level. As such, if the more restrictive settings are applied here external sharing will be disabled across the tenant or restricted to pre-authorized external users assigned by tenant administrators. Basically, the settings will override the settings in the sections below. Navigate to Azure Active Directory > External entities > External collaboration settings. The following options are presented.
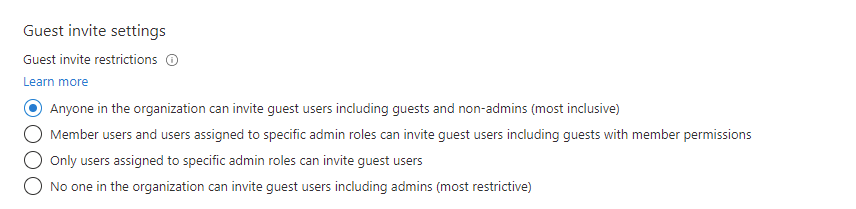
- Anyone in the organization can invite guest users including guests and non-admins (most inclusive). This is the most permissive setting, and is enabled by default. It allows all tenant users and guests to invite any external guest user.
- Member users and users assigned to specific admin roles can invite guest users including guests with member permissions. This setting is more restrictive and allows tenant users and authorized guests to invite other guests.
- Only users assigned to specific admin roles can invite guests. This provides for more controlled access that is managed by administrative users.
- No one in the organization can invite guest users including admins (most restrictive). This will prevent files from being shared with all users. This restriction applies to administrators as well.
Microsoft 365 Admin Center
The Microsoft 365 Admin Center has two key areas that need to be reviewed when configuring a tenant for controlled shared access. The first area concerns allowing users to add guests to the organization. When enabled users can invite guests to be members of Microsoft 365 Groups. Microsoft 365 groups promote collaboration between groups of people. When a Microsoft 365 group is created the following items, among others, are set up:
- A SharePoint site
- A SharePoint document library
- A distribution group
- Shared mailbox
- Shared calendar
- OneNote notebook
- When a Team is set up it, creates a corresponding Microsoft 365 group
Guests will typically receive email messages sent to the groups and will be able to collaborate and access files that are in the group.
This is accessed by clicking on Settings > Org settings > Security & privacy > Sharing. The following option is presented:
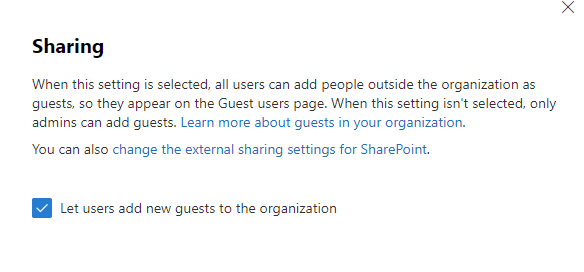
Note that if this is enabled, the guests that users add do not show up as guest users in the Microsoft 365 Admin Center or in Azure AD Admin Center. Those guest entries are reserved for tenant administrators who add guests to the tenant. The key difference is that when an admin adds guest users, those users become part of the directory and are available for other users to include and invite to other M365 groups or Teams. Sharing policies can be defined to allow for users to invite guests or they can be restricted to allow only guests that have been added to the tenant by administrators.
The second setting in the Microsoft 365 Admin Center is for controlling Microsoft 365 Groups. Microsoft 365 Group configuration is accessed by navigating to Settings > Org Settings > Services > Microsoft 365 Groups.
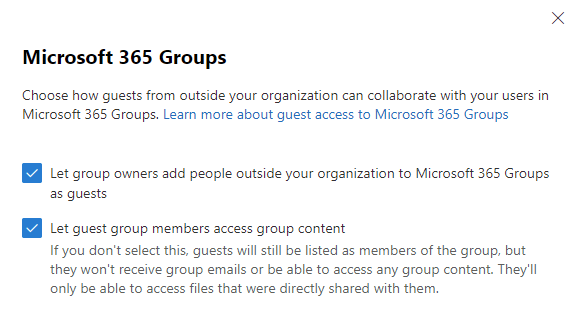
SharePoint / OneDrive
The next place to configure and control external file sharing is in the SharePoint Admin Center. Sharing policies are access by expanding Policies > Sharing. The following options are shown.
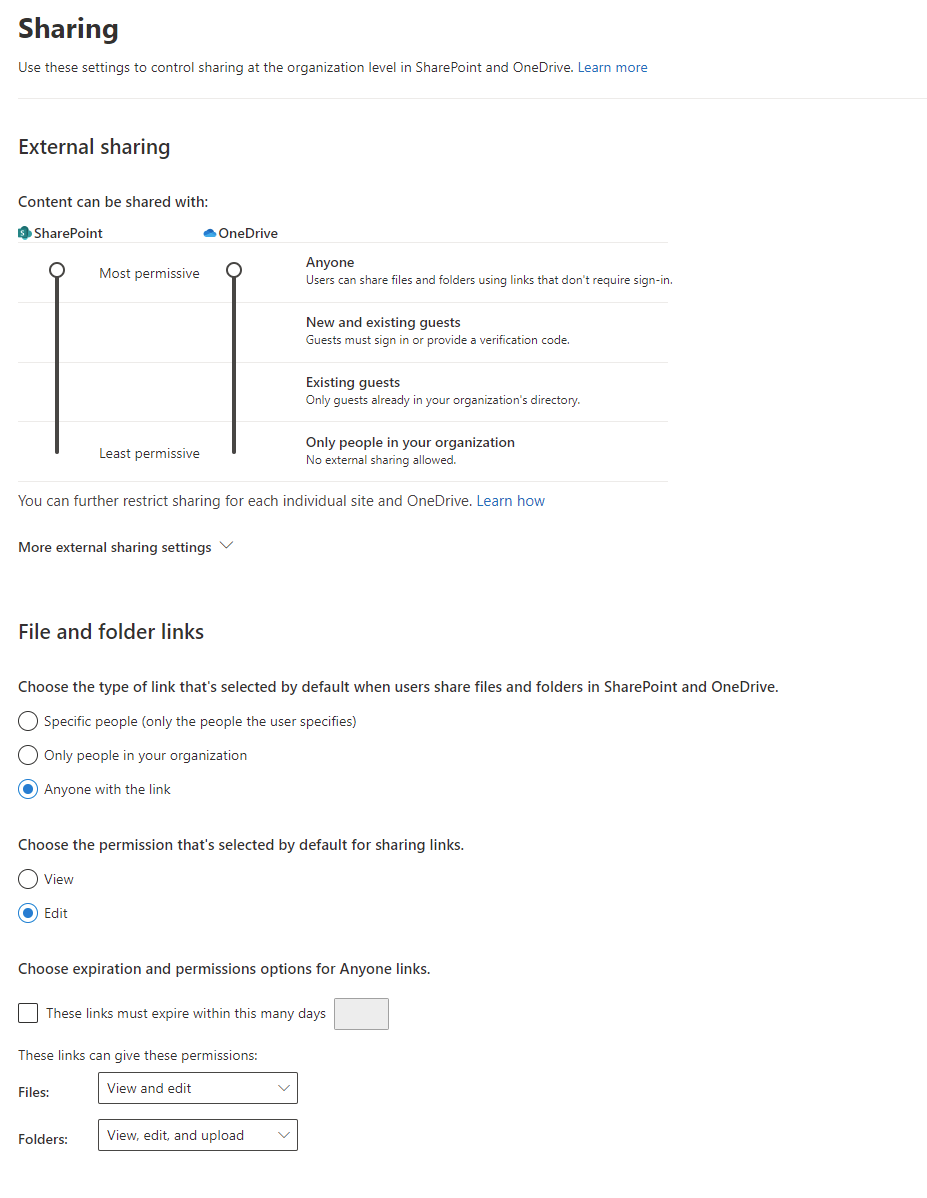
Start by setting the two sliders that control shared access to SharePoint and OneDrive. Note that OneDrive settings cannot be more permissive than SharePoint settings. The options are as follows:
- Anyone: By default, both allow the most permissive access, meaning users can share files and folders with anonymous users. This is rarely a good option to allow.
- New and existing guests: allows for users to add guest access. This provides for some security in that users must either sign in to M365 or provide a verification code that is emailed to the guest user.
- Existing guests: The only guests that files/folders can be shared with are guests that have been added to the tenant by administrators. Users cannot indiscriminately share with anyone they like. This provides for a much higher level of control in that only authorized guests can be added. This option, though, may be difficult to maintain over the long run. Note, there is an additional option to allow guests to self-register. This type of guest access is beyond the scope of this blog.
- Only people in the organization: This option disallows external access altogether.
The remaining options for controlling external sharing below should be reviewed. Most significant is choosing expiration and permissions options for Anyone links. Here you can set expiration dates for links, meaning after a predetermined length of time the links to access documents will become inactive thus preventing access to the files/folders.
Additionally, expand the More external sharing settings option. This provides additional methods to control access. A common setting is to limit external sharing to specific domains. This can be defined by allowing only specific domains or blocking specific domains. Allowing only specific domains can be useful to limit users to share with only the domains of customers or partners, for example. Another useful option is to allow users who are members of specific security groups to share externally.
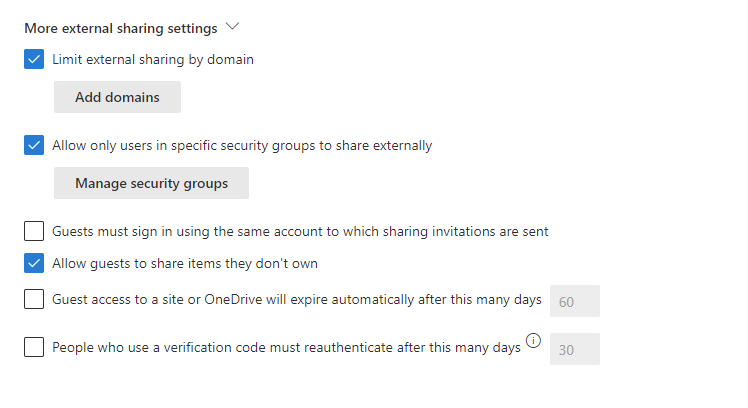
Teams
Since Teams stores its files in OneDrive and SharePoint, Teams policies will respect the settings that are applied in the SharePoint Admin Center. There are, however, additional collaboration settings that should be reviewed for Teams that go beyond file sharing. These can be found in from the Teams Admin Center go to Org-wide Settings > External access and Org-wide settings > Guest access.
Setting up a Microsoft tenant requires proper planning and configuration before granting users access to it. Hopefully, this article has provided some clarity around external file sharing.